Quick analysis write-up on the link between Lazarus and WannaCry
Here is a short post on what I found out about the “link” between Lazarus and WannaCry. To me, the function referenced looks a lot like only a generator for a TLS 1.0 client hello.
On 2017-05-15 19:02 Neel Mehta tweeted the following:
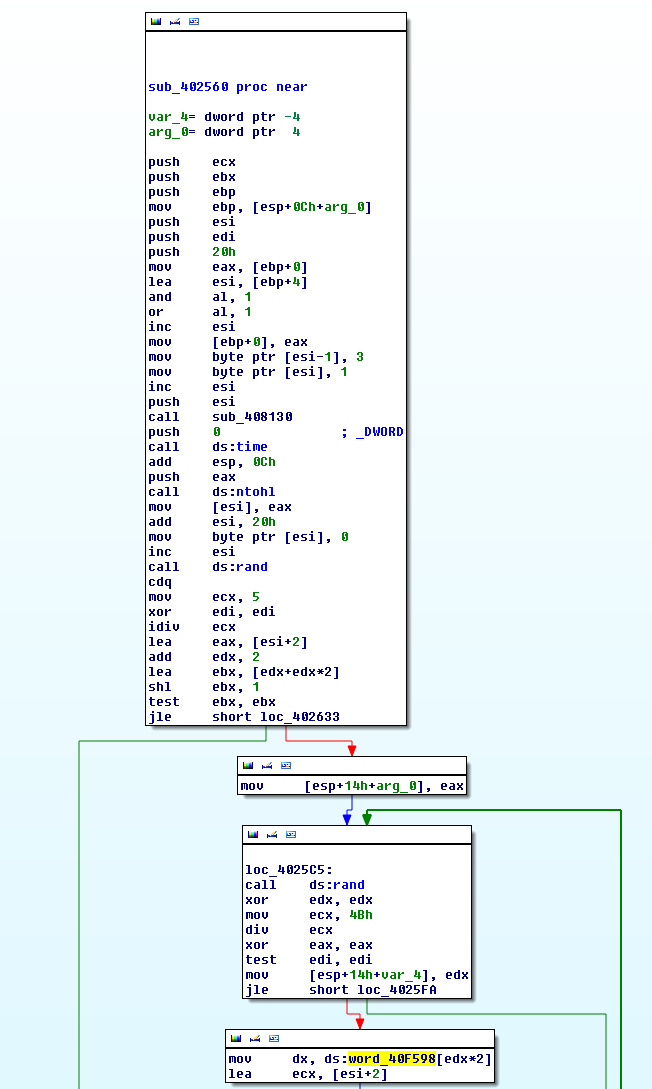
If we have a closer look at 0x402560 in the February WannaCry sample (the function referenced and compared by some others), we see the following:
For my point, of special interest is the buffer highlighted:
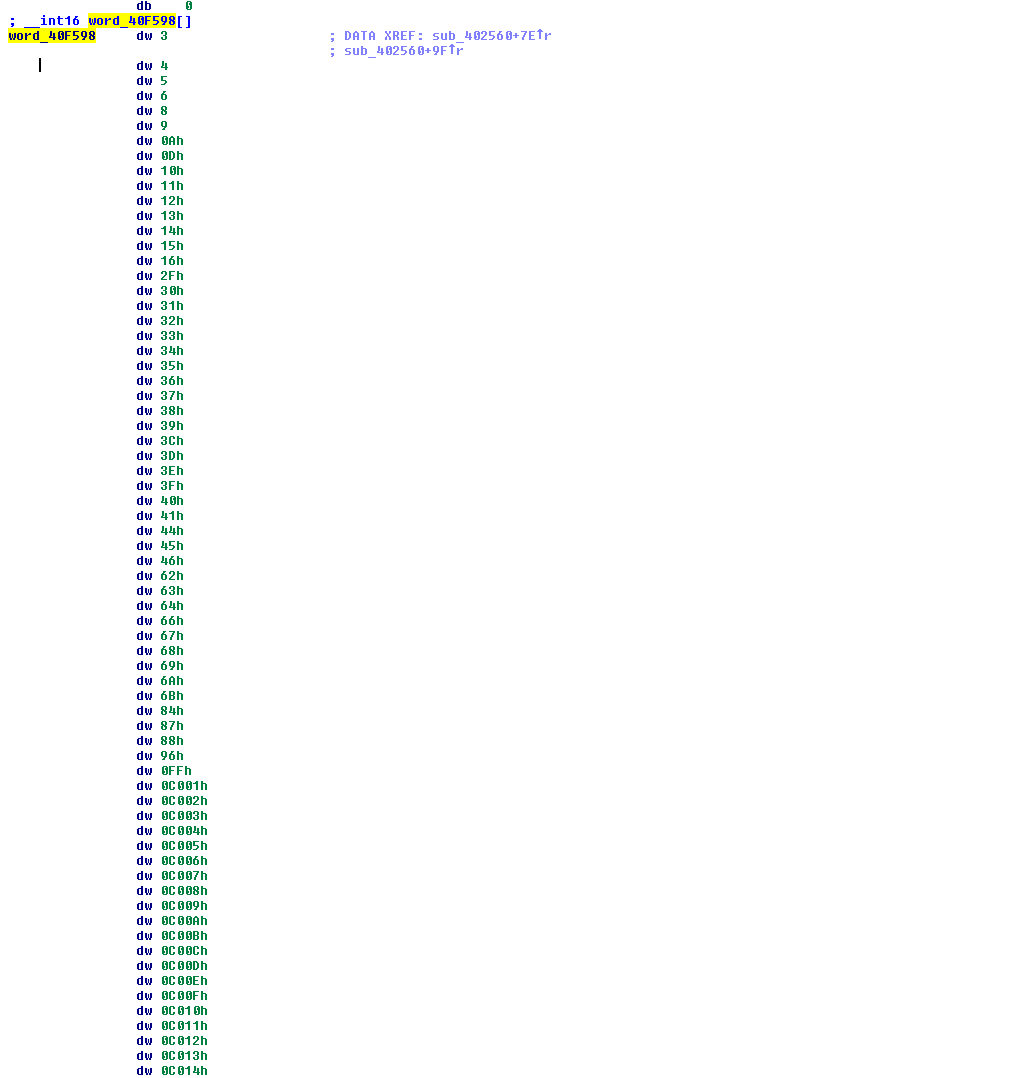
Searching for some of these constants, we can quickly infer that they likely infer to OpenSSL ciphersuites, as listed for example here.
While there are TLS fingerprinting projects, I did not find matches for the embedded selection.
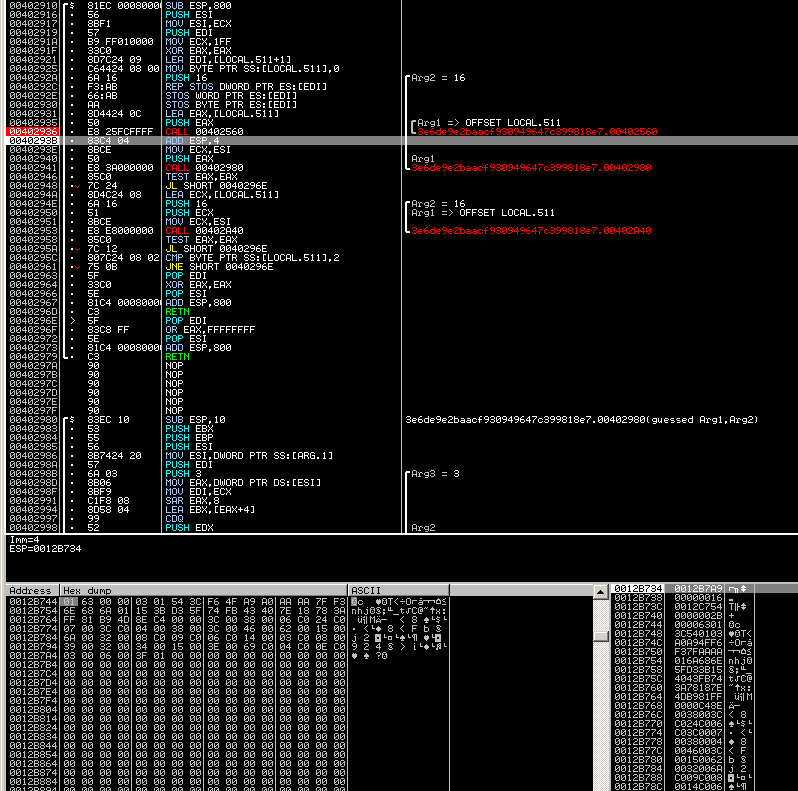
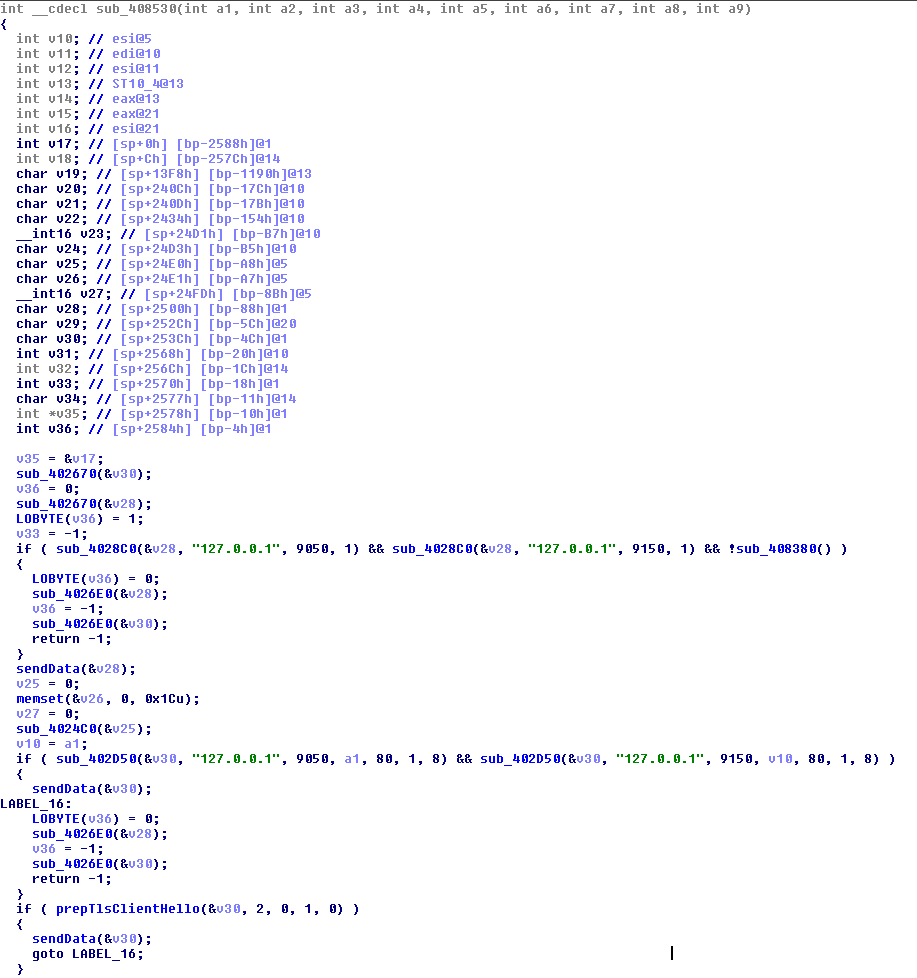
Now, if we run this function in a debugger like Olly:
You will see that it generates a buffer like shown in the lower left corner (dump window).
Here is a couple more of these, annotated:
So the structure pretty much matches what you would expect from a zero-len session-id TLS Client Hello.
Some more indicators for this claim that we look at Client Hellos is the usage in a function a bit up in the call chain:
Here our buffer generated by 0x402560 is send to localhost listening on typical TOR ports.
Maybe some part of the TOR communication capability (or adapter) was directly embedded in this earlier version of WannaCry?
Assessment:
While I agree that the compiled functions from both samples (A: WannaCry, B: Lazarus) originate very likely from the same source code and that they were compiled with similar tooling (there are some more indicators for this in how the generated code look likes, e.g. padding, thunks, …), the exclusivity of the code defines the strength of the link.
This function provides a rather generic network-based functionality (yet in a strongly specific way), so I would not be surprised if eventually the respective source code appears as being publicly accessible in some corner of the wild and open Internet. In that case we could be looking at a super weird coincidence.
Hashes:
3e6de9e2baacf930949647c399818e7a2caea2626df6a468407854aaa515eed9- WannaCry, February 2017766d7d591b9ec1204518723a1e5940fd6ac777f606ed64e731fd91b0b4c3d9fc- Contopee